Sending Emails with End-To-End Encryption
Emails are inherently insecure. Consider a scenario where you are receiving the results of a blood test from your doctor via email. There is no guarantee that the email was not viewed by anyone else before it reached your inbox unless it was encrypted. This page demonstrates a very simple way of sending messages with end-to-end encryption ensuring no one but the actual recipient will be able to see the message.
Design Goals
Before discussing how to encrypt emails, let's talk about a few design goals for such a system.| Privacy | No one but the intended recipient should be able to open the message. Not even administrators or a junk filtering email system. |
|---|---|
| No Plugins | No plugin should be required to open the original message. It uses software that is commonly available on every computer or mobile device. |
| Mobile Access | Recipients should be able to open the message on their mobile devices, running on iOS, Android or Windows. |
SSL/TLS A misconception
Many individuals incorrectly think they can achieve end-to-end encryption when using SSL/TLS. SSL can only encrypt in-transit data. Consider the image below as an example: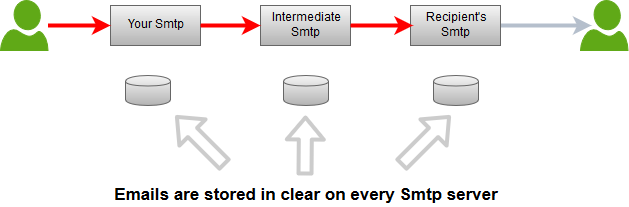
Legend
| Red | Encrypted |
| Gray | Not Encrypted |
Using Xeams for End-To-End Encryption
Starting from v6.6 of Xeams, users can send encrypted emails to recipients on the Internet without using any special software on the client's machine.Sending Emails with Encryption
Users can compose emails using their favorite email clients, such as MS Outlook or Mozilla Thunderbird on desktop, Apple or Android mail on a mobile device, or any web-based interface. The only additional step they must take is to put a configurable trigger word in the subject line. For example:
Your tax returns for 2024 confidentialIn this example, the trigger word is
confidential.
Encryption Methods
Xeams offers two method for end-to-end encryption for emails:
Recipients will need to view their encrypted emails through your Xeams web interface. The following bullets demonstrates the flow of events:
- Sender composes an encrypted email containing the trigger word in the subject.
- Recipient is asked to create a password.
- Recipient will sign in to your Xeams web interface to view their encrypted emails.
Companies looking to provide end-to-end encryption that is also FIPS 140-2 compliant, can use this method to transfer sensitive documents with anyone on the Internet.
Xeams will convert an email into a password-protected PDF document, which can only be view by the recipient with a password. The following bullets demonstrates the flow of events:
- Sender composes an encrypted email containing the trigger word in the subject.
- Recipient is asked to create a password.
- The original email is converted into a password-protected PDF file and will be attached to another message.
- Recipient will only be able to view the original email after decrypting the PDF file with their password.
Sensitive Keywords
As a company policy, you can define certain words/pattern as sensitive. For example, if an email contains a social security number or a credit card number, you may want to force your users to encrypt that message. Using the following steps you can force your users to use encryption:- Select Plugins under Home and click Manage button
- Check Require encryption for sensitive content
- Specify keywords in the field for Sensitive Words
- This field can accept patterns specified as regular expressions
Specifying Passwords
There are multiple ways to specify a password for an end-to-end encrypted email.
- Ask the recipient to create a password for their email on your system. Click here for details.
- Create passwords in Xeams for different recipients. Administrators as well as end-users can pre-define passwords for the recipients. Click here for details.
- Put the password in the subject line, enclosed with parentheses. For example:
confidential(secretPwd). This option only works if your Xeams is configured to use the PDF method.
Configuring End-To-End Encryption
Following steps demonstrates how to configure your Xeams:
- Log in to your Xeams web interface as the administrator
- Click Home/Plugins, and click the Manage button for End-To-End encryption.
- Ensure this feature is enabled and specify a Trigger word. End users will have to put this word in the subject line to trigger encryption.
