Preventing Hackers From Stealing Passwords
Intruders enter through available doors. The more doors you have the more cautious you need to be to ensure no one can steal the identities of your users. In technical terms, these doors are analogous to servers listening for clients to connect. A typical email server has at least 3 doors: SMTP, IMAP, and POP3. This blog discusses steps every administrator needs to take to ensure your server is not vulnerable to hackers looking to steal passwords.

The two most common ways to steal passwords are:
- Performing a dictionary attack, which is done by guessing millions of combinations of user id and passwords with hopes that they will eventually get a hit.
- A man-in-the-middle attack, which occurs when someone secretly watches communication between two parties.
Preventing Dictionary Attacks - SMTP Server
The most effective way of preventing a dictionary attack is to close unnecessary doors. In other words, disable features you don't need in your server. One such "door" is SMTP Authentication.
Do you need Authentication?
Authentication in an SMTP server is only required if in-house users send outbound messages through this SMTP server. In other words, it is not required when:
- You only get inbound emails from the Internet
- In-house users either connect to a different SMTP Server or connect on a port other than TCP/25. In second case, you can disable authentication for port 25
but leave it on for the other port.
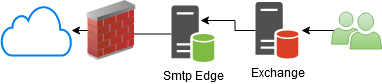
For example, refer to the image on right. Since every user connects to Exchange server to send and receive their email, there is no need to enable SMTP authentication on the Edge Server, which is responsible for filtering spam messages.
Therefore, disabling Smtp Authentication when no one is using it will simply close an available door that could have otherwise be exploited.
How to check if authentication is enabled on your SMTP
Every SMTP server advertises its supported features, including authentication. Use the following script on any Linux machine to query the features supported by your SMTP server.echo "EHLO host.example.com QUIT" | nc $1 $2Save the above script to a file called checkSmtp.sh and change its permissions to executable using the following command:
chmod +x checkSmtp.shThis script takes two parameters: host name and port. The following command shows an example of how to run the script:
./checkSmtp.sh mail.yourCompany.com 25Below is a screenshot showing the results of this command when ran against an SMTP server that accepts authentication.
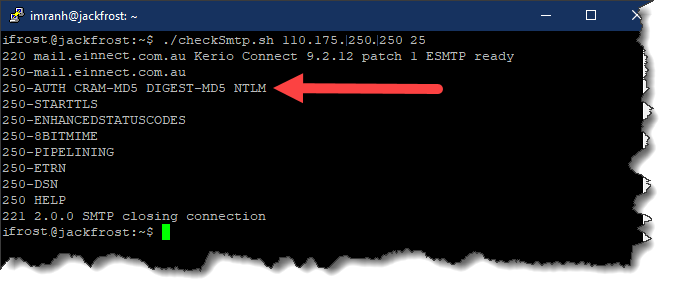
Notice the line that says:
250-AUTH CRAM-MD5 DIGEST-MD5 NTLM
The existence of this line confirms authentication is enabled on the SMTP server.
Caution
Some email servers do not advertise the AUTH mechanism unless encryption is used. Since you cannot connect to an SMTP server with encryption using shell scripts alone, we recommend using the Email Sender utility to test. Keep in mind that it is very easy for a malicious user to encrypt the communication. Therefore, it is important to test your server using encryption.Preventing Dictionary Attack - IMAP/POP3
Unfortunately, disabling authentication during IMAP/POP3 communication is not possible. Therefore, the only way to prevent a dictionary attack for IMAP/POP3 is to proactively detect invalid password attempts from repeated IP addresses and block them.
Performing a dictionary attack manually is not practical. Therefore, there is a very good chance a computer program on the other end is sending thousands of authentication requests within a short period of time. In such cases, configure your email server to block the IP address if more than a predefined number of attempts are made within a few minutes.
Besides IMAP and POP3, this technique is also very useful for SMTP server and you should definitely consider turning it on. Off course your SMTP server needs to support this feature in order for you to use it.
Preventing Man-In-The-Middle Attack
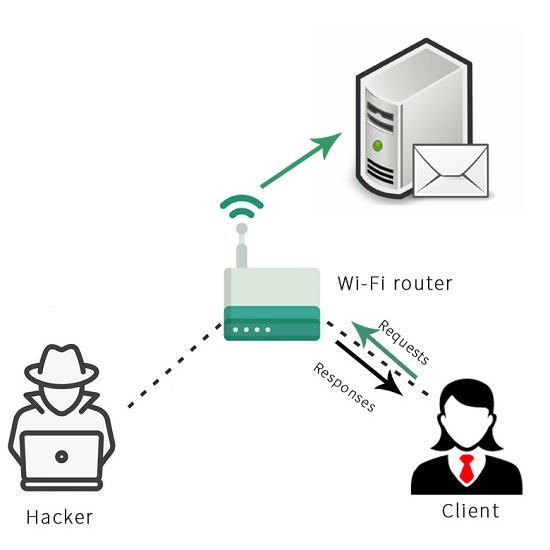
The most common method of stealing someoneís password is to have them go through a monitored network.
Consider the following scenario as an example:
- John is traveling to a foreign country and is in desperate need for a free Wi-Fi hotspot.
- He has a stopover at Londonís Heathrow Airport and finds a hotspot that says "Free Heathrow Guests".
- He immediately tries connecting through it and it works. He loves it.
- What he did not realize is that a hacker, Kevin Mitnick, was sitting closeby with a laptop that created a fake hotspot with a name matching the airport. Now he is able to capture every communication between your mobile device and your server.
Encryption to The Rescue
Using encryption can mitigate the problem described above. Encryption ensures two things:
- It ensures no one can watch the communication between two parties. In the above example, these two parties are Johnís iPhone and his email server.
- It ensures the identity of the server. In other words, John can rest assured he is in fact communicating with his own server rather than Kevinís fake hotspot. This identification will only work if Johnís iPhone is configured only to trust signed certificates.
How to Ensure Everyone Uses Encryption
Often users are careless about using encryption. Since their end-goal is to get the device connected to the server, they often ignore the settings related to SSL/TLS and end up connecting to the server without encryption.
One way to ensure users are using encryption is to monitor their connectivity logs. Email Server, such as Xeams, can notify administrators of every user who is not using encryption when connecting to any listening server, including SMTP, IMAP, and POP3. Click here to watch a short video on this topic.
Summary
Hackers are always seeking to crack user id and passwords so they can be misused. By implementing proactive approaches at the server level, administrators can ensure their users are connecting in a sure manner. Additionally, by closing unnecessary doors on the server administrators can reduce their exposure to hackers. Therefore, it is important to use an email server, such as Xeams that facilitate administrators to stay proactive regarding their email infrastructure.
How do you ensure users connect to your email server using a secure mechanism mitigating the risk of getting their credentials stolen? Use the comments section below to answer.
| Created on: | Sep 2, 2020 |
| Last updated on: | Jul 1, 2025 |
