Blocking fake invoices scam from PayPal
Recently, a new type of scam email has been detected that lures the victim to call a fake custom support number. Once the victim calls this phone number, the perpetrator convinces them to install malicious software on their computer to eventually extort money. This page analyzes how this scam works and what you can do to block such emails.
How It Works
Before discussing the nitty-gritty details of formulating the attack, let's identify the actors involved.
- PayPal - Acting as a facilitator because their services are used to generate fake invoices
- Microsoft - Acting as a facilitator. Often, users fail to follow best-practice guidelines, resulting in their accounts being stolen.
- Victim 1 - Who's account is stolen
- Victim 2 - This is the potential victim who will call the 800 number mentioned in the email. This victim can potentially lose thousands of dollars, if not more.
Next, let's analyze a sequence of events.
- First, scammers hijack existing accounts on Microsoft Exchange Online. These accounts are hijacked because they lack security features like MFA or because scammers steal them while surfing online over unprotected networks. These stolen accounts give scammers the vehicle they need to send and receive emails to the actual victim.
- Next, they create fake invoices using a PayPal account and send them to the email address they hijacked earlier on Microsoft. In other words, the generated invoice goes not to the actual victim but to Microsoft's server.
- The scammer then creates a server-side rule in Exchange Online to forward these incoming emails from PayPal to the actual victim.
Dissecting The Message
The following screenshot displays a sample email.
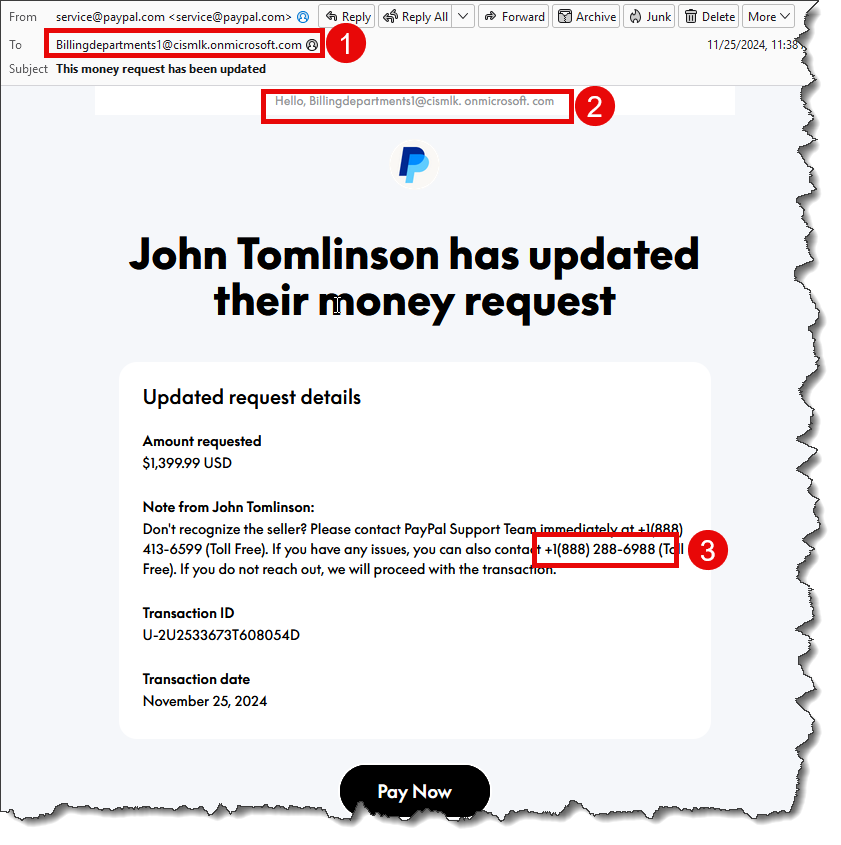
Notice a few characteristics of this sample:
- The "To" field does not belong to you but to the fake address the perpetrator created on Microsoft Exchange Online. This address appears in the email header and the body of the message, as shown with markings 1 and 2.
- PayPal allows writing a custom message in the Notes area. This is where the phone number appears, where the victim is expected to call. This is displayed by marking number 3.
Why Spam Filters Fail to Block Such Messages
Legitimate companies: PayPal and Microsoft generate and forward these fake invoices. In other words, technologies like DKIM, SPF, and DMARC will always pass since the messages originate from authorized servers.
Why SPF fails to block
The victim will receive this email from a valid account hosted on Microsoft. In the example above, the domain name cismlk.onmicrosoft.com contains the following SPF record:
v=spf1 include:spf.protection.outlook.com -all
Therefore, every message originating from a Microsoft server will be considered legitimate.
Why DKIM fails to block
The scammers are smart enough not to change the content of the email, which could invalidate a DKIM signature. The DKIM signature for the example email above is set to the following value:
DKIM-Signature: v=1; a=rsa-sha256; d=paypal.com; s=pp-dkim1; c=relaxed/relaxed; q=dns/txt; i=@paypal.com; t=1732632029; h=From:From:Subject:Date:To:MIME-Version:Content-Type; bh=QS5nBV4tfjKpf8OaUAUxN3X3cAmNxcFu9VLTdyUD2b0=; b=g42RaHAgufIHGSmMwns1D3rHp1aqbEYK9om7CUOWOIVf9CGX0eGufBlSyZ+C0gGz ukX/Y/BoVCOHDDPqRUHZq1TF0ekRpbrcyqtyv8VOYjRgyS+eL4snrfYGsqE7AyA4 kp5StyO3zkkgsFL6eaGzPXxouQlHWpcuTkS33hH8nMkl7v/oQcjBjFKQPBwgrLBw 3bEg4gpCj1y4jMLdiXephJpSJovc51ymRAUEoT4Gfthj2BJxqdNWTmugNiB3YdW2 r6g2QIF6XRVCCGn0d2jfip8BoFbxZHLcVCoAcci9DyqEace7JtDGWB8m8cgZN1LP eNlXaXDX+uhJn4wPZ7u5jQ==;
This is a valid DKIM signature for any message originating from PayPal. Therefore, the victim's spam filter will treat it as legit.
How to Block Such Messages in Xeams
Since the conventional methods of validating an email fail, you must use the unconventional content filtering methods available in Xeams.
Custom Filter
Ensure the Fake Receipts filter under Filter Management/Content Filters/Custom Filters is checked with a score of at least 150.
Adding a Content Filter To Parse Header
Add a Header Filtering using the following steps:
- Log in as the administrator
- Click Filter Management/Content Filter/Header Filters
- Create a new Header Filter with the following values:
- Select "To" for the field name
- Specify ".onmicrosoft.com" for the search string
- Assign a score, such as 200, and select Ends with for the operator
- Save
Adding scores for BCC
The recipient's email address appears in the BCC field. Shared email addresses, such as sales@yourcompany.com or support@yourcompany.com, seldom receive emails with the recipient in BCC. In such cases, you consider adding the following rule.
- Click Filter Management/Content Filters/Custom Filters
- Scroll down to the rule for BCC Rejector.
- Click the link to add new addresses for this rule and add emails like sales@yourcompany.com and support@yourcompany.com
