Product » A free email server for Windows and Linux » Knowledge Base
Document information
| Document ID: | 5225 |
|---|---|
| Subject: | Best Practices - Prevent hackers from guessing passwords |
| Creation date: | 7/3/18 12:42 PM |
| Last modified on: | 1/19/22 10:50 AM |
Prevent hackers from stealing passwords
Any publicly facing server is vulnerable to attacks from the Internet. These attacks are typically severe against well-known servers like SMTP and HTTP since the TCP/IP port for these services is publicly known. Hackers know that most email servers will contain user login information allowing them to send outbound emails, increasing its vulnerability. This article talks about some best practices to prevent hackers from guess passwords through your email server.Most email servers contain at least 3 TCP/IP servers: SMTP, POP3, and IMAP. Some servers, such as Xeams, also include an HTTP server. As the saying goes, "your network is as strong as your weakest link." Therefore, it is essential you secure every path of entry from the Internet.
The timeline for an attack can be broken into two phases:
- Attack prevention - pro-active approach
- Recovery from an attack after it occurs
Attack prevention
Consider the following tips to secure your email server minimizing the risks of a breach.Disable SMTP Authentication
A common mistake is to enable SMTP Authentication on your primary SMTP port (TCP/IP 25)
even when it is not needed. Consider the following email flow diagram demonstrating a classic example
when SMTP Authentication should be disabled in Xeams.
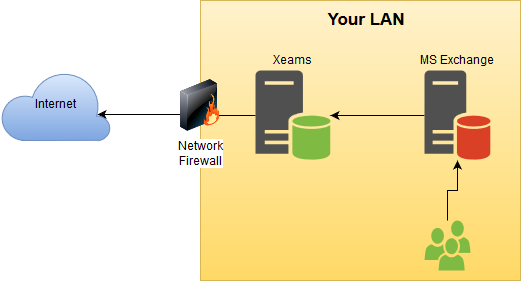 Since no user on the Internet needs to authenticate with their credentials to the SMTP server in Xeams,
consider disabling SMTP AUTH for port 25. This is done by following the steps below.
Since no user on the Internet needs to authenticate with their credentials to the SMTP server in Xeams,
consider disabling SMTP AUTH for port 25. This is done by following the steps below.

The following assumptions are made in this example:
- You're using MS Exchange as your primary email server
- Users use MS Outlook or the OWA to send their outbound emails. In either case, emails go to Exchange first and then are forwarded to Xeams before reaching its final destination.
- You have configured Xeams to accept relaying from the IP address where Exchange is running
- The regular SMTP server in Xeams handles both inbound and outbound emails
- Log in to Xeams web interface as admin
- Click SMTP Configuration under Server Configuration
- Uncheck the box for Allow SMTP Authentication
command
unrecognized error if they attempt to send a user id/password.
Let Xeams Block Malicious IPs
Log in as the administrator to the web console, click Server Configuration and select the Advanced tab. Then,
check the box for Block Malicious IP Addresses. When checked, Xeams will proactively block the IP address that detected
to send malicious requests.
Disable IMAP/POP3
Another mistake administrators make is to leave the POP3/IMAP server running even when no
user connects to fetch emails. Consider disabling POP3 and/or IMAP servers if no one connects to them.
Check logs
Xeams contain many logs that will help you see if something out of ordinary is happening. For example:
- Intrusion Detection logs - Click here for details.
- InvalidPasswordAttempts.log - contains attempts made by users trying to guess passwords.
- SuccessfulLogins.log - contains login attempts and if they are using a secure connection.
Use Custom Ports
When it comes to HTTP(S), IMAP and POP3, you can always ask your users to connect to a non-default port.
Since hackers do not know the port, number of attacks will go down tremendously.
Unfortunately, you will not be able to do that for SMTP server, since every incoming email is sent to
port 25.
Configure Alerts
Go to Manage Alerts under Server Configuration and ensure alerts are properly configured. Additionally, make
sure the email address specified for the administrator in Xeams is correct. Xeams often generates email if something
out of ordinary is detected.
Recovering From An Attack
Consider the following steps if you think someone has gained access to a user account and is now misusing it to send their junk messages.Identify the User
The first step in mitigating the risks from a compromised user account is to identify the actual account. Consider the following
tips for identifying a user.
- Authenticated Messages report lets the administrator know if a particular user has sent more than a pre-determined number of emails in an hour. An email alert is also sent to the administrator once the user goes beyond a specified threshold.
- Check
SMTPConversation.logand look for theAUTH LOGINcommand sent by the SMTP client. The following lines will contain user's account name encoded in BASE64. - Daily and Weekly reports also give a good summary of messages that are sent and received.
Clear Outbound Queue
When a user id is compromised, someone on the Internet will be able to send their junk through your server. As a result, you
will see quite a few non-deliverable messages sitting in the outbound queue. Click Manage Outbound Queue under
Message Repository and delete the unwanted messages. If there are too many files, you can manually delete the files
at the OS level. On Windows, these files are stored in
C:\Xeams\OutboundMailQueue. On Linux, the path is
/opt/Xeams/OutboundMailQueue
Add a comment to this document
Do you have a helpful tip related to this document that you'd like to share with other users?
Important: This area is reserved for useful tips. Therefore, do not post questions here. Instead, use our public forums to post questions.
